Virtual CISO vs. In-House CISO: Making the Right Choice
Choosing between a Virtual CISO (vCISO) and an In-House CISO depends on your organization’s size, budget, and security needs. Here’s…
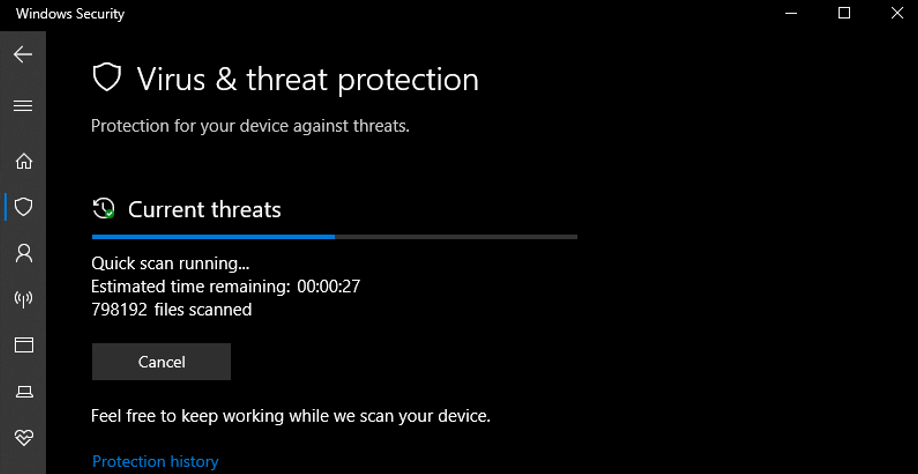
Balancing Security and Performance: Do We Really Need Regular Full Scans?
We previously recommended Microsoft Defender for Endpoint full scans as a configuration best practice in this article, since that is…
5 Challenges of Breach and Attack Simulation
Breach and Attack Simulation (BAS) helps organizations identify 30–50% more vulnerabilities than traditional methods. However, implementing BAS comes with challenges.…
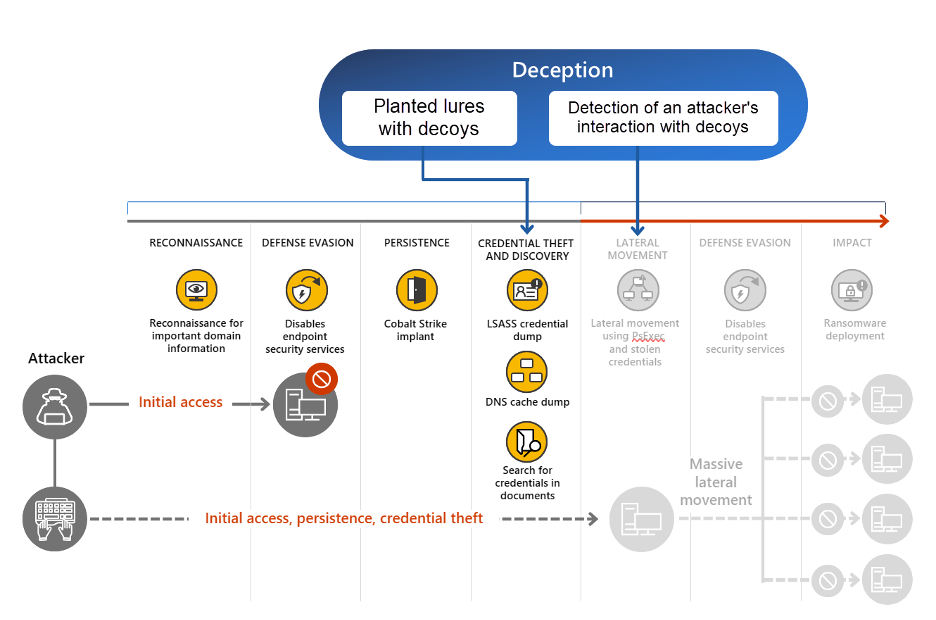
How Microsoft Defender’s Deception Feature Detects Cyber Threats Early
Microsoft Defender for Endpoint includes a powerful Deception feature, designed to enhance early threat detection and response capabilities. This blog post will…
Optimizing Microsoft Defender for Endpoint on Resource-Constrained Devices
In today’s rapidly evolving cybersecurity landscape, protecting all endpoints within an organization is crucial. However, many businesses face unique challenges…
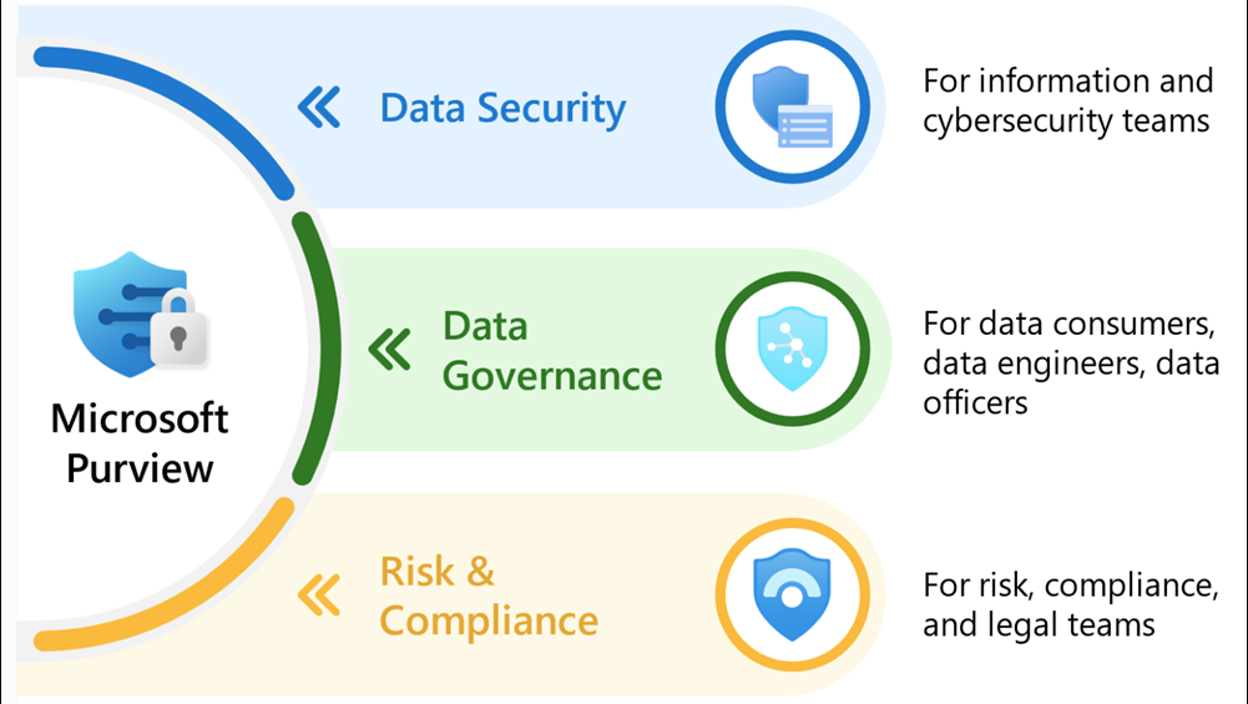
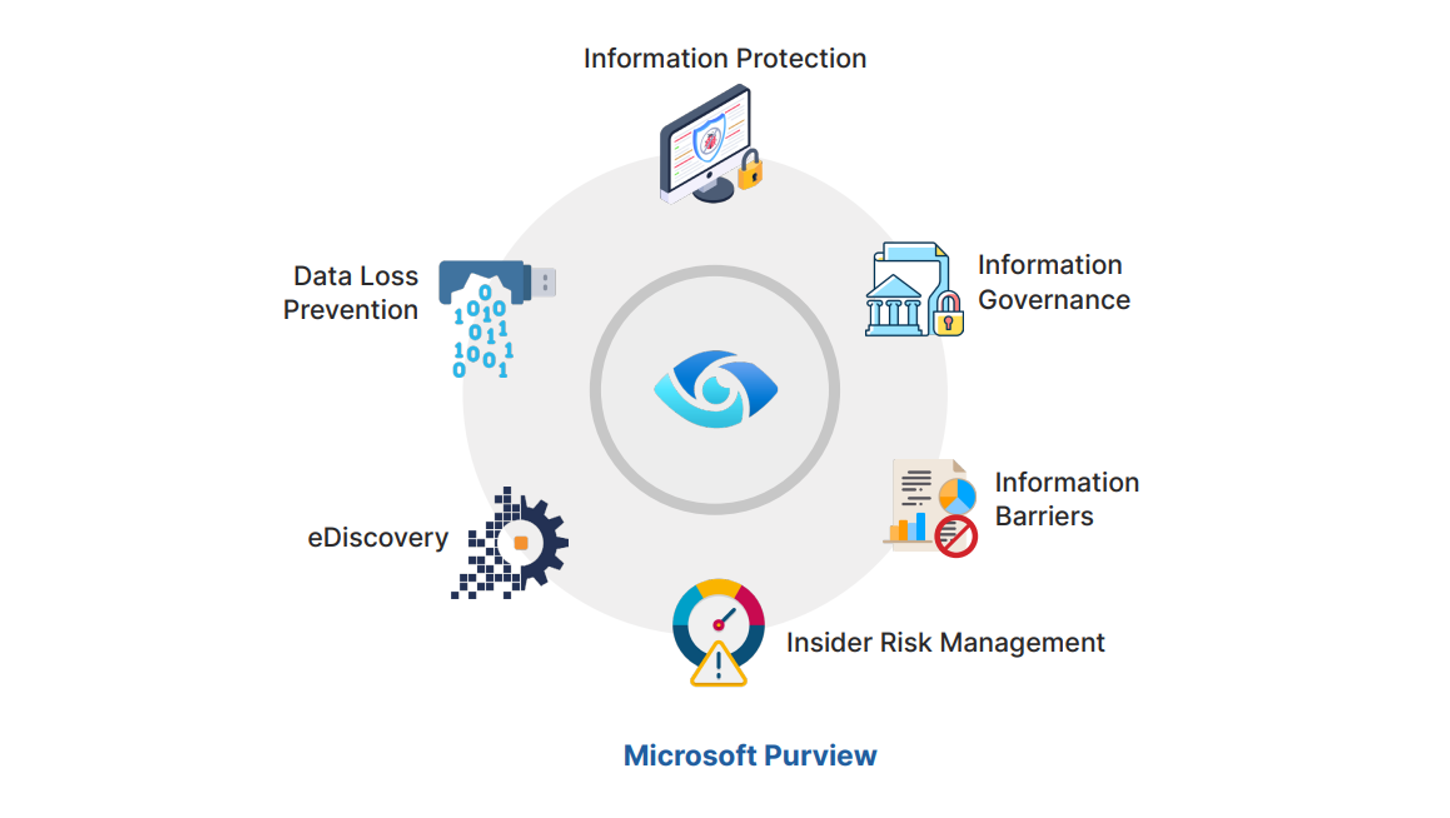
Data Loss Prevention with Microsoft Purview
Why Should We Use Data Loss Prevention Solutions? Data Loss Prevention (DLP) is crucial for organizations in highly regulated sectors…
Onboarding MacOS devices to Purview Using Intune
As previously mentioned, a successful DLP implementation program should cover all 3 main data exfiltration channels which are Web, Collaboration…
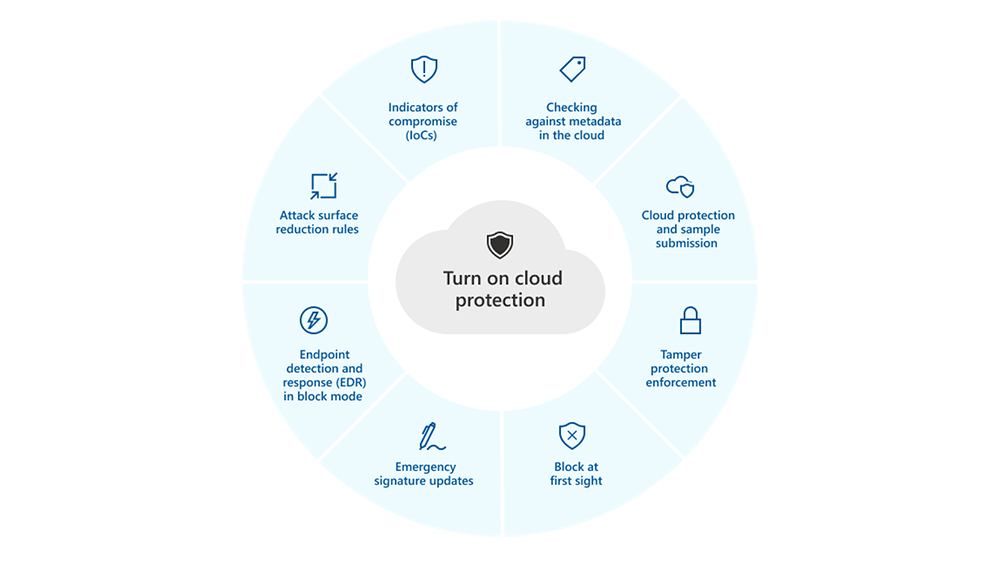
MDE Antivirus Policy Best Practices
Why Customizing Microsoft Defender for Endpoint Antivirus Policy Settings is Crucial Microsoft Defender for Endpoint (MDE)is a powerful endpoint security…
Protect Your Emails Leveraging Antispam, Anti-phishing, SPF, DKIM and DMARC
In today’s digital landscape, email remains a critical communication tool for organizations. However, it is also a primary target for…
TISAX Compliance: The Essential Guide for Automotive Suppliers
Gain a competitive edge in the automotive supply chain by learning everything about TISAX: compliance, its benefits, assessment levels, and…
7 Most Essential SCPs to Enforce for your AWS Environment
Locking Down Your Cloud: Essential Service Control Policies for Robust AWS Security The need for ensuring the safety and compliance…
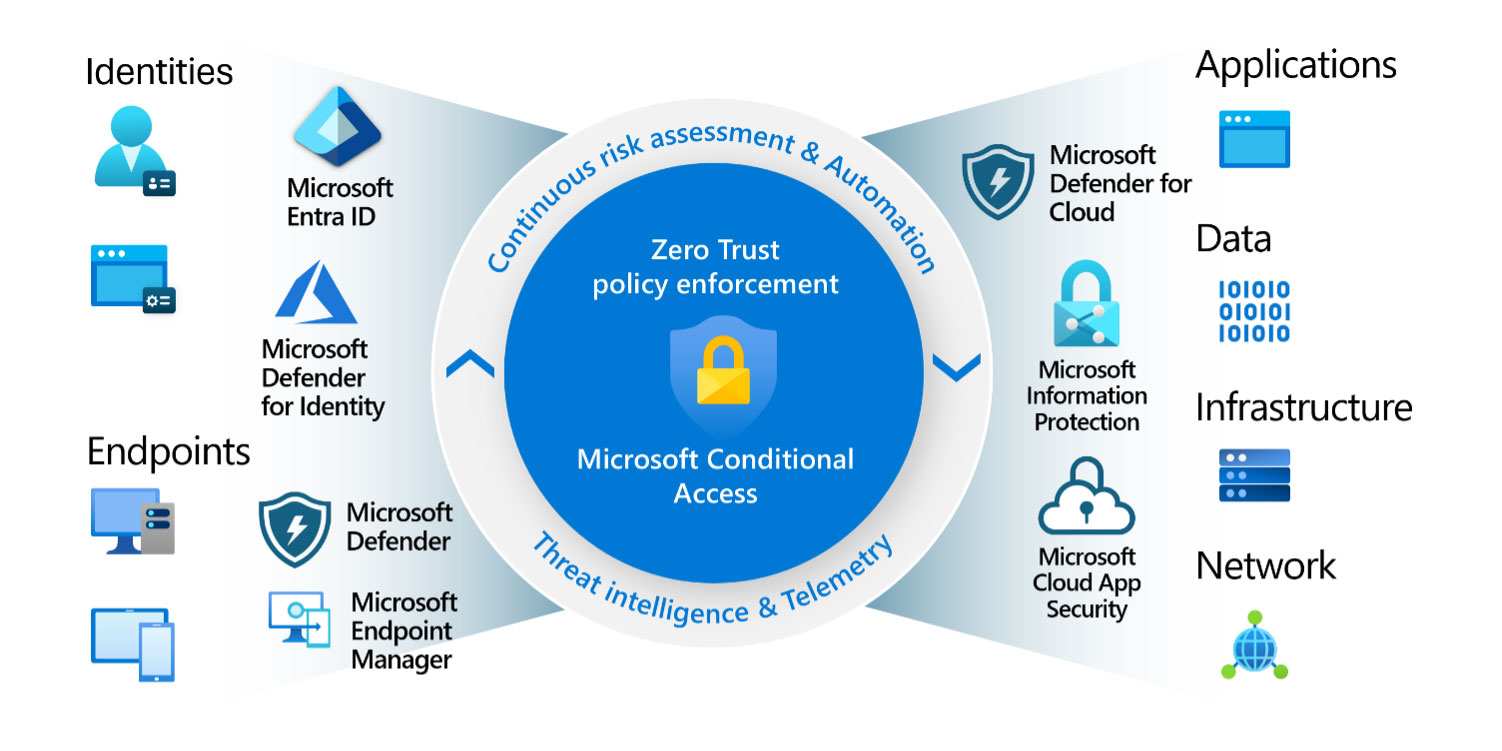
Deployment of 10 Essential Conditional Access Policies
Deploying Conditional Access in your organization can be (and should be) a rather long task. This is because rushing into…
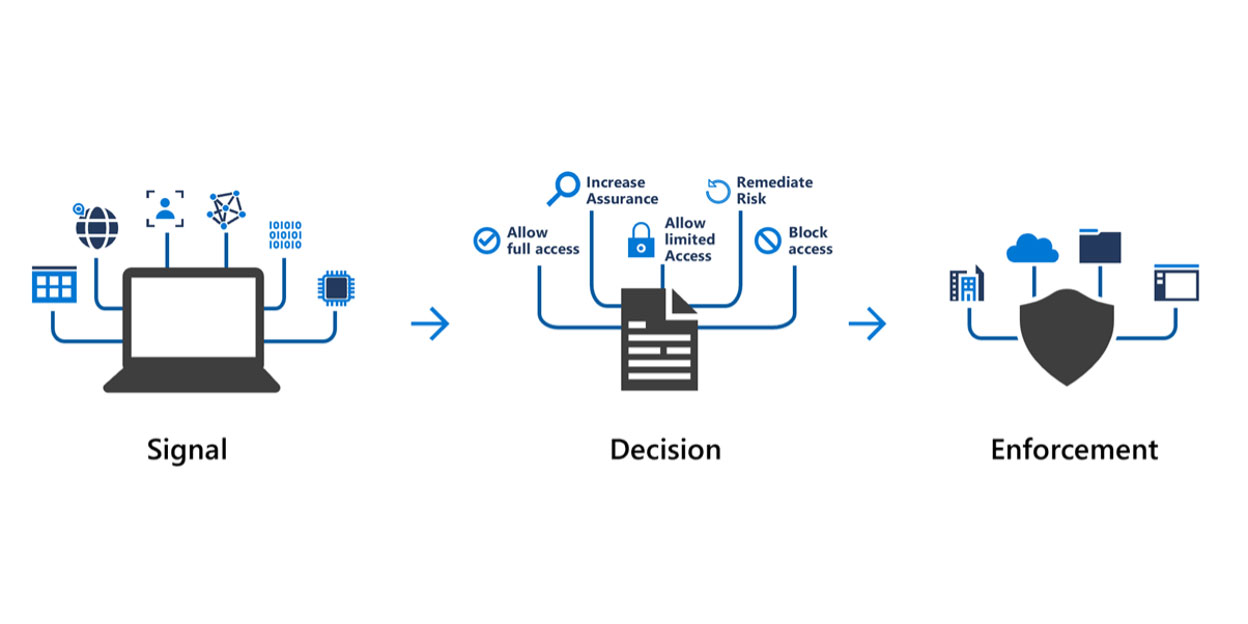
Introduction to Conditional Access
Introduction to Conditional Access More and more applications are made available to the users on public internet with organizations embracing…
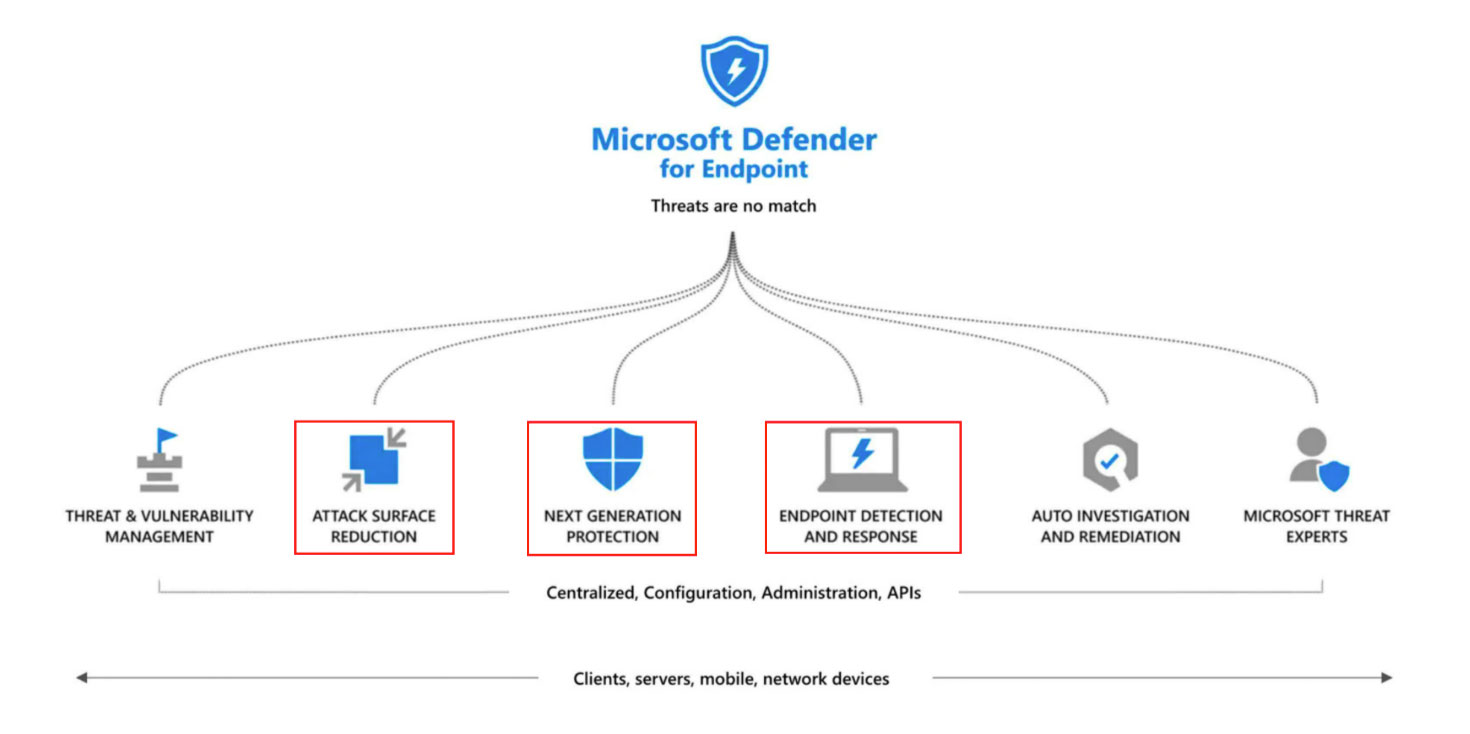
Microsoft Defender for Endpoint Attack Surface Reduction
What is ASR? One of the capabilities of Microsoft Defender for Endpoint that is often overlooked because of its fancy…