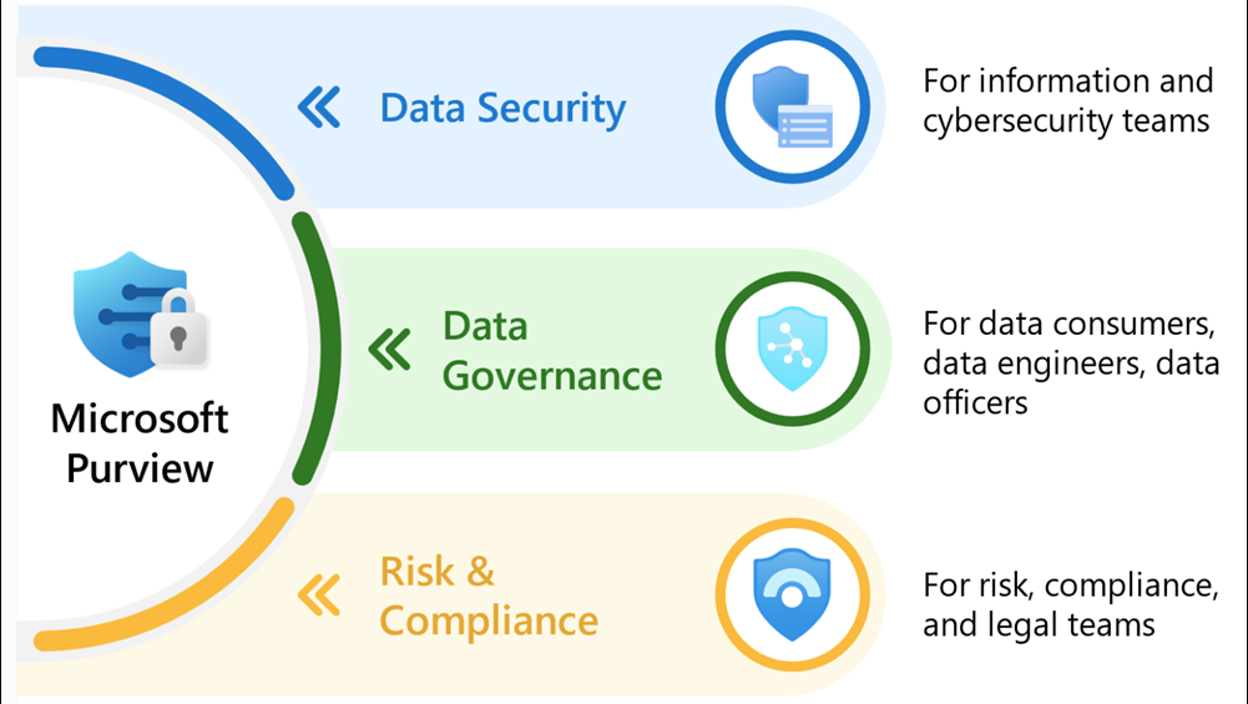
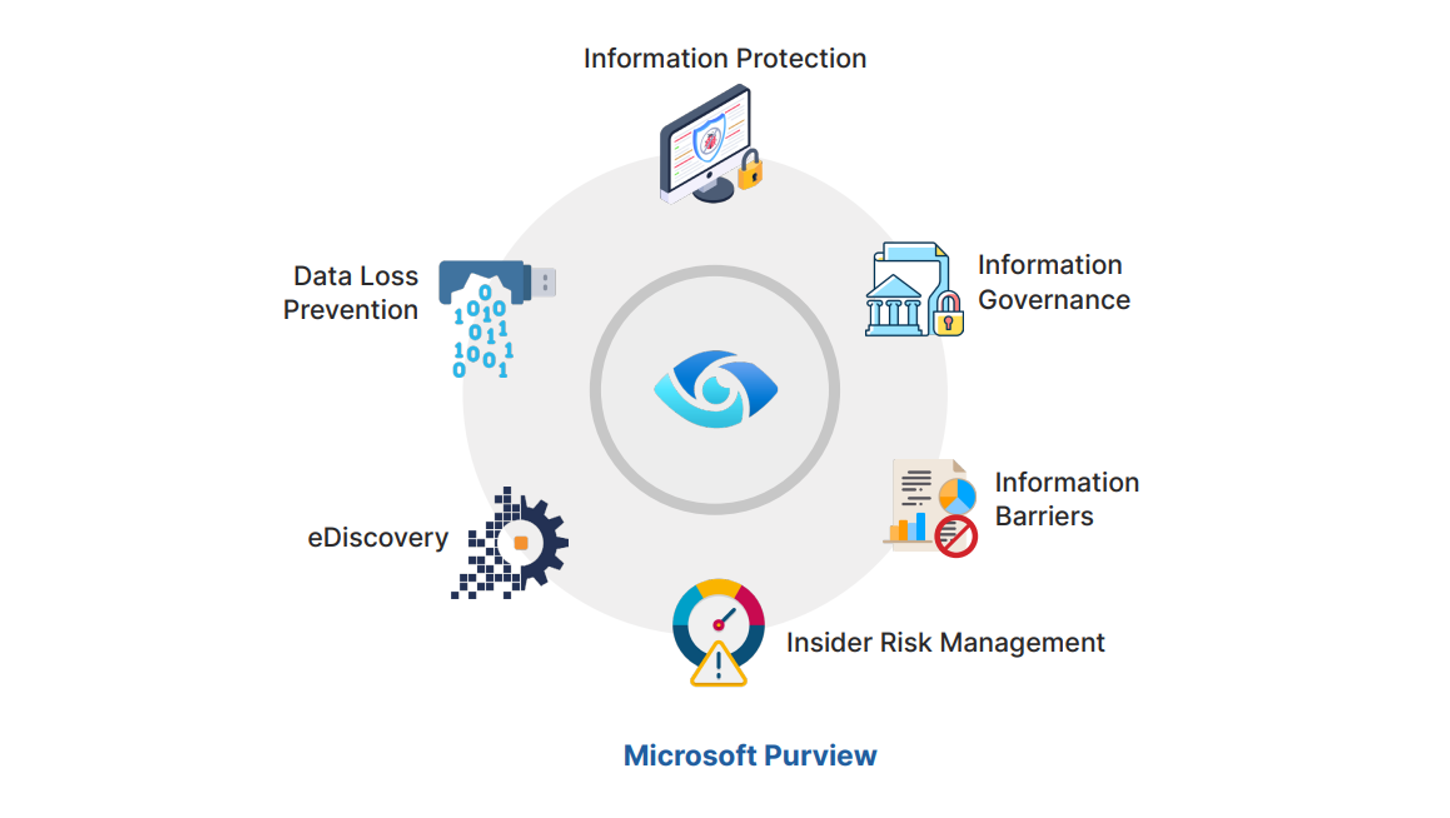
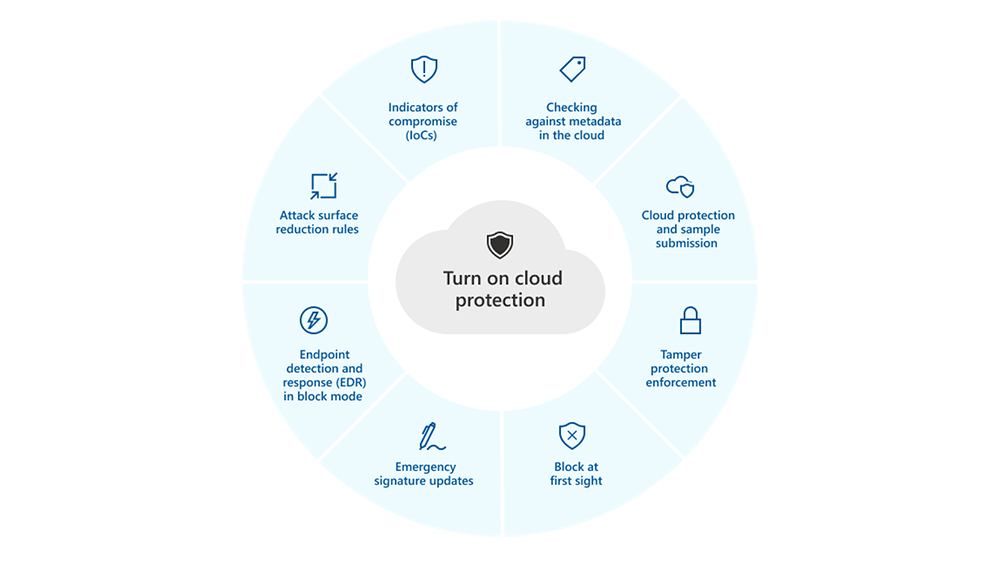
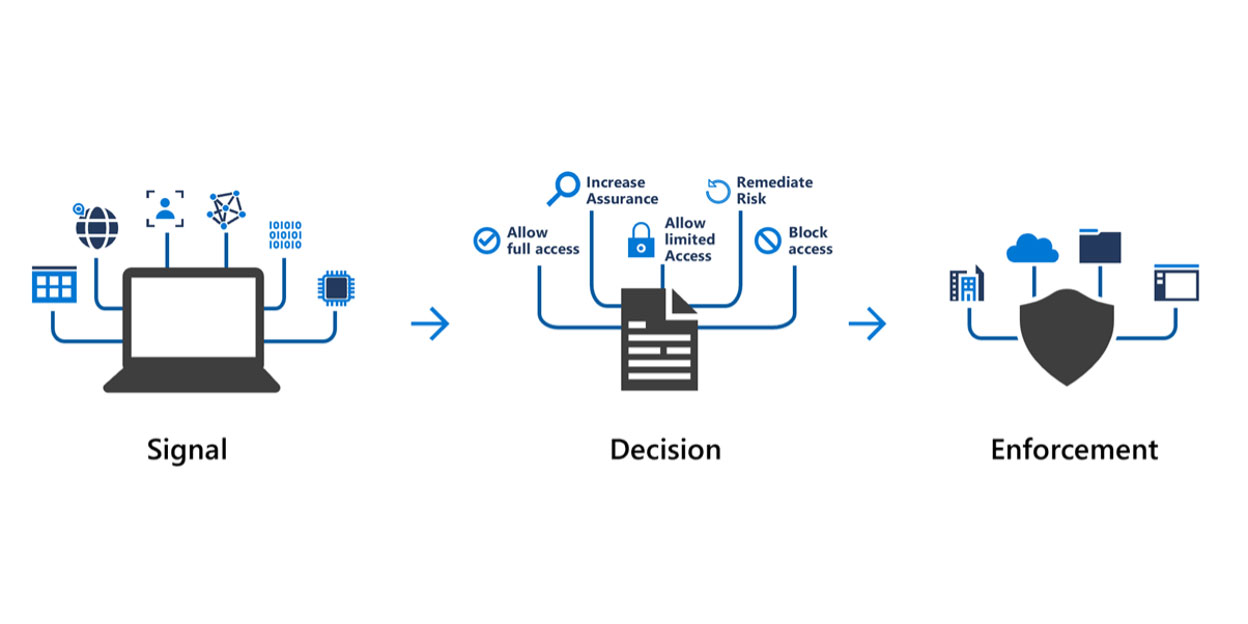
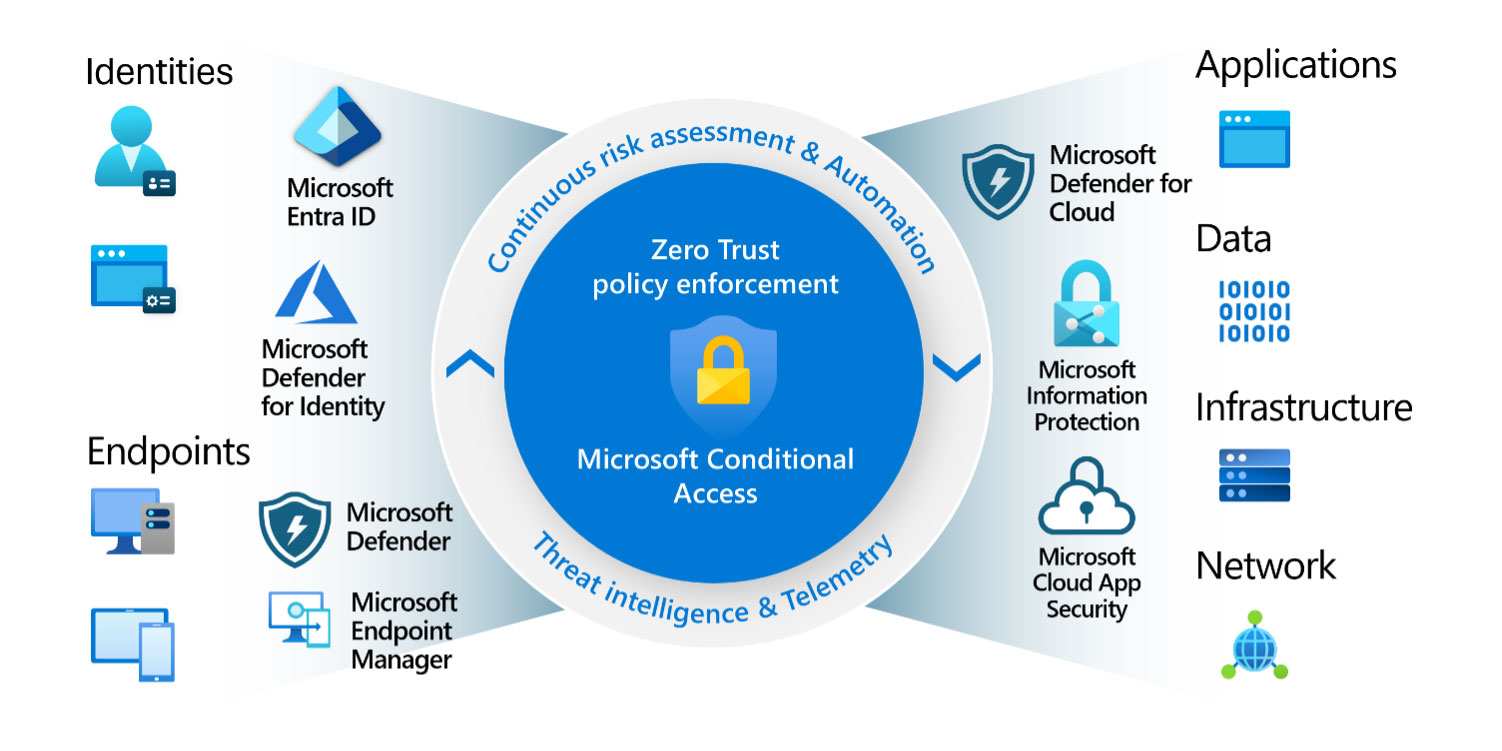
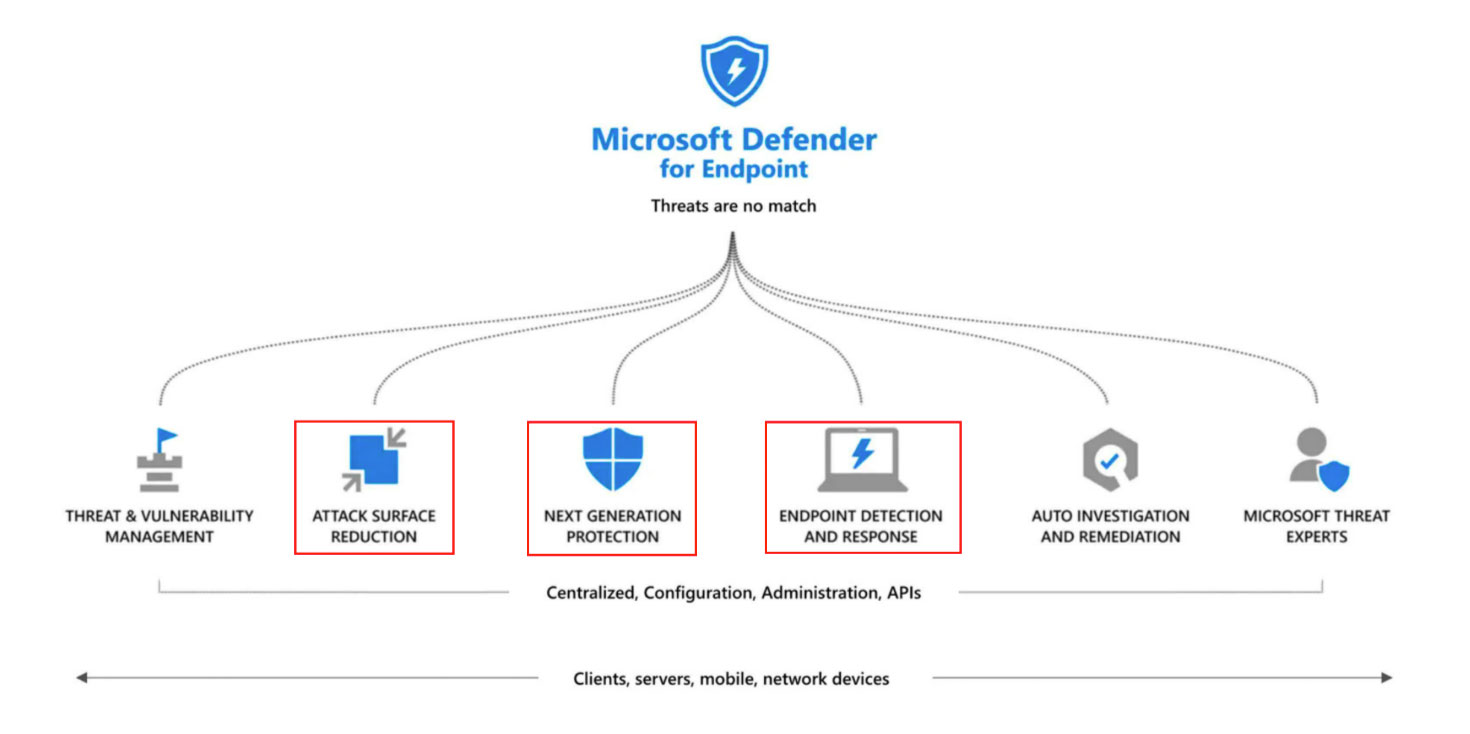
Data Loss Prevention with Microsoft Purview
Why Should We Use Data Loss Prevention Solutions? Data Loss Prevention (DLP) is crucial for organizations in highly regulated sectors like banking, financial services, healthcare, government, or those investing in research and development. In these environments, sensitive information, such as personal data or trade secrets, must be protected against unauthorized access or unintentional leaks. Implementing…