As previously mentioned, a successful DLP implementation program should cover all 3 main data exfiltration channels which are Web, Collaboration and Endpoint with all their subcomponents.
When it comes to endpoints, onboarding Windows workstations to Purview is quite easy. If your organization provides MacOS devices to your users, these devices should also be onboarded to Microsoft Purview as well. This blog article walks you through on how to achieve that.
Before we start it is important to know that Microsoft Purview is favoring Windows endpoints when bringing DLP controls. This means not all DLP capabilities that are possible with Windows endpoints are available for MacOS computers. The table below summarizes the unsupported features for MacOS systems.
| Setting | Sub-setting | Windows Endpoints | MacOS Endpoints |
| Setup evidence collection for file activities on devices | Set evidence cache on device | Supported | Not Supported |
| Network share coverage and exclusions | NA | Supported | Not Supported |
| VPN settings | NA | Supported | Not Supported |
This article focuses on onboarding MacOS devices to Microsoft Purview using Microsoft Intune. To achieve that, MacOS devices should already be onboarded to Microsoft Intune and Microsoft Defender for Endpoint must also be installed on the MacOS devices.
Prerequisites
- You must have the necessary privileges to execute the actions on Microsoft Intune and Microsoft Purview. To simplify it, we gained Security Administrator and Compliance Administrator privileges.
- Windows Defender for Endpoint must be running on the MacOS devices.
- The MacOS devices must have been onboarded to Microsoft Intune using Company Portal application.
- The macOS devices must be running macOS 10.12 (Sierra) or later.
After we make sure that all the prerequisites are met, there are three more steps to finish the operation.
1. Gathering the Configuration Packages
The onboarding operation requires a minimum of 5 MacOS Configuration policies to be created in Microsoft Intune MacOS Configuration menu.
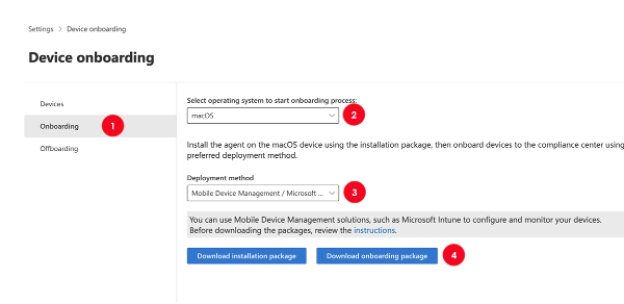
The first place to gather the configuration files is Microsoft Purview portal Device onboarding page. This menu can be reached following Settings Device Onboarding Onboarding menu items.
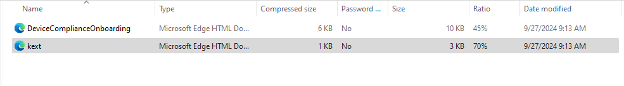
Inside the onboarding package there are 2 configuration files, Device Compliance Onboarding and 3rd party Kernel Extensions (kext).
After this step, you should follow this link to download 2 more files, as shown in the following screenshot.
The mdatp.mobileconfig file is a bundled configuration file, replacing several separate configuration files. Microsoft recommends using this file to make it simpler and avoid human error during configuration.
In the end of the preparation step, we must have 4 files.
2. Creating Configuration Policies for MacOS Devices
Provided that we have already installed Company Portal and Microsoft Defender for Endpoint on MacOS computers, we can start configuring the Configuration Policies based on downloaded files.
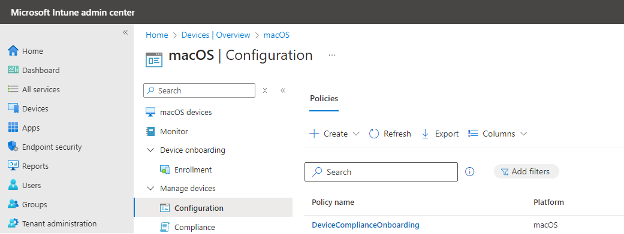
To achieve this, we must go to Configuration Policies for MacOS devices. The path is Home > Devices | Overview > macOS.
We should then create profiles with each of the previously downloaded files, 4 in total. We must click on the + Create button to create new policies and follow along. The configuration is straightforward, but Microsoft did not document everything in their documentation.
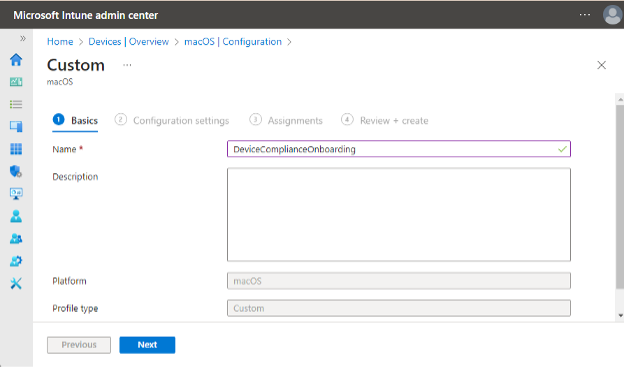
At the first step, a Custom Template must be selected for MacOS operating system.
It is a good practice to name the configuration policies with the name of the file they are created from. In our example, it will be as follows.
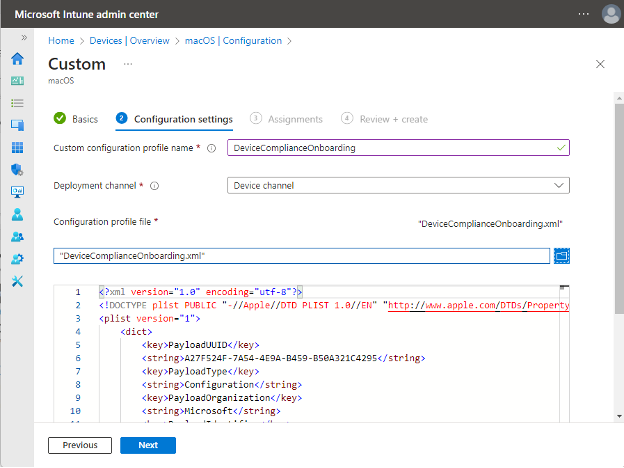
We can use the same name in the second step. Deployment channel must be chosen as “Device Channel”. If the file path is correctly given, the content of the configuration file will appear in the box.
In the last configurable step, the scope of the configuration policy must be defined.
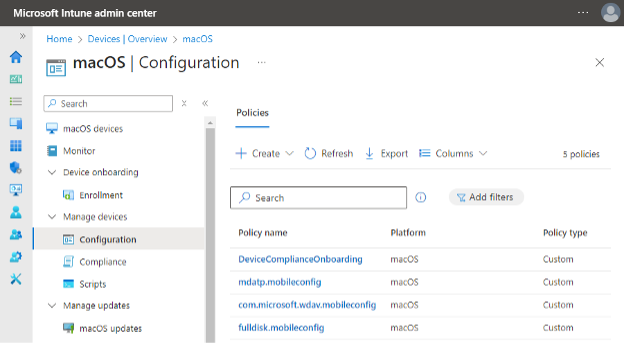
After successfully creating all the configuration policies, it should look like the following.
At this point we should give it at least an hour so that policies are propagated on all computers.
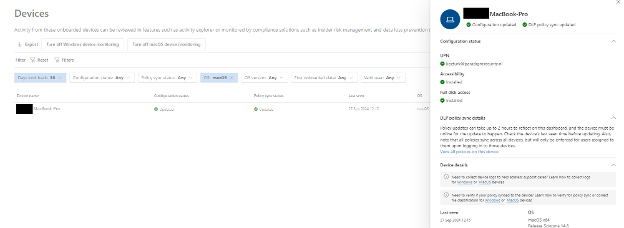
3. Verification
At the end of the hours, we should navigate to Microsoft Purview Device Onboarding Screen. All the fields should be looking OK for Microsoft Purview to work without problems on MacOS computers.
Conclusion
This article explains how MacOS computers in your organization can be protected with Microsoft Purview. We advise you to test your DLP policies on onboarded computers to make sure that configured policies are working as expected.
Do not hesitate to contact us about your queries or if you need support in your deployments.