In today’s rapidly evolving cybersecurity landscape, protecting all endpoints within an organization is crucial. However, many businesses face unique challenges when securing non-traditional devices with limited hardware resources, such as those found in IT/OT environments. This article explores how to effectively implement Microsoft Defender for Endpoint (MDE) on these resource-constrained devices, ensuring robust security without compromising performance.
Understanding the Challenge
Many organizations rely on devices with limited CPU and RAM capabilities, particularly in industrial environments and operational technology settings. These devices require special consideration when implementing advanced security solutions like Microsoft Defender for Endpoint
Microsoft Defender for Endpoint: A Versatile Solution
Microsoft Defender for Endpoint is an enterprise-grade security platform designed to prevent, detect, and respond to advanced threats. Its versatility makes it suitable for devices with constrained resources, including those running Windows 10 and Windows 11
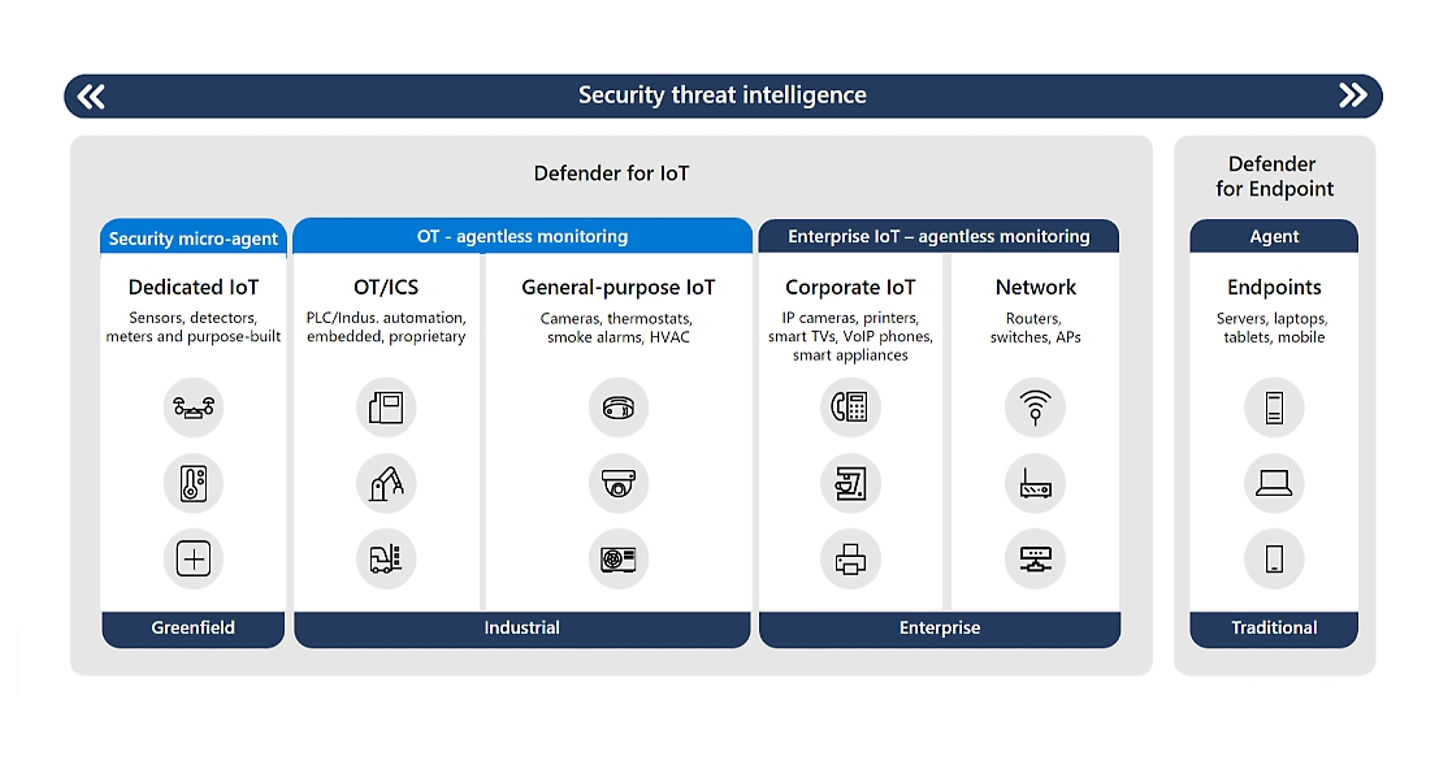
Minimum System Requirements
Microsoft Defender for Endpoint is an enterprise-grade security platform designed to prevent, detect, investigate, and respond to sophisticated threats. With built-in flexibility to support devices with limited hardware capacity, it offers a tailored solution for IT/OT environments. Key benefits include:
- Advanced threat detection and prevention capabilities.
- Customizable settings to optimize performance on low-resource devices.
- Seamless integration with existing security infrastructure.
- Agent-based vulnerability scanning (Additional license required)
MDE Minimum System Requirements
To ensure successful deployment, your lab devices should meet these minimum specifications:
- Operating System: Windows 10 (Enterprise/Pro) or Windows 11 (Pro/Enterprise) version 1809 or later.
- CPU: 1 GHz dual-core processor.
- RAM: 2 GB.
- Disk Space: 1 GB free.
- Network Bandwidth: 100 KB/s minimum.
For devices with constrained resources, consider disabling non-essential services and optimizing background processes.
Network Connectivity
Microsoft Defender for Endpoint requires access to various online services for updates, threat intelligence, and diagnostics. Ensure that these key domains are accessible:
| Service | Fully Qualified Domain Names (FQDNs) | Ports | Purpose |
| Defender for Endpoint | *.security.microsoft.com | 443 | Communication with MDE portal |
| Cloud Service | *.windowsupdate.com *.microsoft.com | 443 | Updates and patches |
| Diagnostics | *.wdcp.microsoft.com *.wd.microsoft.com | 443 | Endpoint diagnostics |
| Threat Intelligence | *.prod.security.microsoft.com | 443 | Threat and detection updates |
| Security Configurations | *.smartscreen.microsoft.com | 443 | SmartScreen URL filtering |
| Telemetry Services | *.vortex-win.data.microsoft.com | 443 | Telemetry data |
Important Notes:
- These domains should be accessible without SSL inspection.
- Proxy servers must support HTTPS CONNECT for port 443.
- Ensure network latency is minimal for critical communications.
Optional Network Endpoints (For Additional Capabilities)
| Service | FQDN | Ports | Description |
| Defender Content | *.microsoftupdate.com | 443 | Content delivery and signatures |
| Incident Response | *.support.microsoft.com | 443 | On-demand support |
| Device Management | *.azureedge.net | 443 | Defender agent update distribution |
Performance Optimization Guidelines
Computers with limited hardware resources require careful tuning of Defender for Endpoint’s features to minimize performance impact:
Real-Time Protection
Real-time protection must be always kept active. However, its impact on processing resources might be reduced by:
- Limit scanning to critical files and processes.
- Configure exclusions for trusted OT-specific applications.
Excluding folders must be kept at a minimum since malware and malicious actors might target exempted locations to bypass security controls.
Full Scans
- Schedule full scans during non-operational hours.
- Throttle CPU usage to 30%-50% by the configuration option Specify the maximum CPU usage or the registry path: Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Scan
Cloud-Delivered Protection
Cloud-delivered Protection uses Microsoft’s cloud-based analysis for real-time threat detection and response. It relies on constant network bandwidth and may impact devices with limited network capacity. Its use can be optimized by:
- Enabling cloud protection only during high-risk activities.
- Configuring telemetry settings to balance resource usage with effectiveness.
- Enable but limit the frequency of cloud lookups:
Set-MpPreference -MAPSReporting Advanced
Configure cloud protection timeout:
Set-MpPreference -CloudBlockLevel Low
Endpoint Detection and Response (EDR)
EDR Collects detailed telemetry data for advanced threat detection and hunting. This generates higher CPU and memory usage for telemetry collection and analysis. The impact can be reduced by
- Reducing telemetry collection levels to the minimum required for effective protection.
Use Intune or Group Policy to set Basic Diagnostic Data:
Path: Computer Configuration > Administrative Templates > Windows Components > Data Collection and Preview Builds
Policy: Allow Telemetry.
Recommended Setting: Basic.
Set-MpPreference -SubmitSamplesConsent 2
(2: Send data only for known threats.)
Network Protection
Network protection blocks malicious domains and IP addresses. Network protection might increase CPU usage due to URL checks and traffic monitoring.
Optimize or disable SmartScreen or network protection for devices with minimal internet usage.
Configuration:
Adjust Network Protection Settings via Intune or Group Policy:
Path: Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender SmartScreen
Policy: Configure Network Protection.
Recommended Setting: Audit Mode
Data Retention and Forensics
Detailed forensic data for incident investigation is retained 15 days by default. This might cause high disk space usage for logging and telemetry storage. It can be reduced to 7 days.
Reduce log retention time:
Set-MpPreference -ScanPurgeItemsAfterDelay 7
Deployment and Monitoring
When deploying MDE on resource-constrained devices:
- Use appropriate installation methods (e.g., Microsoft Endpoint Configuration Manager, Group Policy)
- Enable low-impact modes for devices with limited resources
- Utilize device tags or MDE management groups to segregate lab devices
- Verify device health and connectivity via the Microsoft 365 Defender Portal
- Monitor resource utilization to ensure MDE doesn’t cause device disruptions
Conclusion
Implementing Microsoft Defender for Endpoint on resource-constrained devices requires careful planning and optimization. By following these guidelines, organizations can enhance their security posture across all endpoints, including non-traditional IT/OT devices, without sacrificing performance. By adopting these best practices, businesses can leverage the power of Microsoft Defender for Endpoint to protect their entire device ecosystem, ensuring comprehensive security coverage in an increasingly complex digital landscape.
